Splunk UF Tagging
Do you have Splunk UF's that are running in a load-balanced manner and/or ingesting other host data (ie. central syslog server)?
Take advantage of Splunk's built-in meta tagging. This meta tag can be used with multiple key::value definitions.
Navigate to ~/etc/system/local within your UF
# ~/etc/system/local/inputs.conf
# Within the [default] stanza, create your '_meta' definition
[default]
....
# _meta = [key1]::[value1] [key2]::[value2]
_meta = static_uf::devForwarder
PLEASE NOTE: For modular inputs, such as Window's event logs, you will need to add it to the stanza.
[WinEventLog://Security]
disabled = 0
start_from = oldest
current_only = 0
evt_resolve_ad_obj = 1
checkpointInterval = 5
blacklist1 = EventCode="4662" Message="Object Type:(?!\s*groupPolicyContainer)"
blacklist2 = EventCode="566" Message="Object Type:(?!\s*groupPolicyContainer)"
renderXml = 1
index = wineventlog
_meta = static_uf::devForwarder
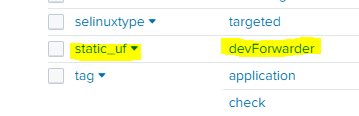
In the image above, you can now see that the UF has a field called 'static_uf' with a value of 'devForwarder' as defined in our [default] stanza. Also, this field is automatically searchable within Splunk without a 'fields.conf' definition.
